Originally published at the NAAIJ on June 2nd, 2014

Follow us on Twitter @NAAIJ
Like us on Facebook NAAofIJ
A campaign is under way to Reset The Net. The hope of this campaign is to emerge in a post June 5th world with a more secure standard of communications. It is common knowledge these days that NSA/CSEC/GCHQ/etc are listening to everything anyone has ever said. Indeed even this very article as I draft it is probably within the reach of the NSA to infringe upon, as Edward Snowden recently alluded to exactly that in his most recent interview on NBC.
An excerpt from the Reset The Net Tumblr
“First, there are tons of ways to fight back against NSA surveillance. Anything that makes the Internet or individuals using it safer and more secure makes mass surveillance harder, for the NSA and for any other government.
It can start with you. These super-easy encryption tools let you talk, chat, and text with pretty strong privacy. If everyone used them, that would go a long way to shutting down mass surveillance. So, be the first. And tell your friends. In the end, beating the NSA could be that simple.”
Most of the tools they recommend I’m quite familiar with myself. I’ll link to a few of them here for those eager to be secure ahead of The Reset.
Secure instant messaging: Pidgin (w OTR plugin, Mobile users Get ChatSecure for Android or ChatSecure for iOS.)
Hide your IP (with exceptions!): Tor (Mobile users Get Orbot for Android.)
Encrypted GSM/SMS: TextSecure & RedPhone (Android only, iOS users get Signal 2.0)
Pidgin is a messaging client that supports numerous protocols. The one I’m using and you should use is XMPP, previously known as Jabber. The XMPP server I use is creep.im, You can add me using [email protected]
Here is a quick pictorial on how to get started with Pidgin.
Click Add…

Fill out the form as shown below, using your own username and password.


I am using Tor in this example. Simply Install Tor and run it, The defaults will work.

If all goes well you will get this screen. This is your actual registration so remember your password.

Confirmation that all is well.

Add your first buddy. Feel free to add myself, [email protected] or the demo account I just made [email protected]

When someone adds you, This is what it will look like.

The OTR plugin gives further security by providing even more encryption and buddy authentication via secret phrases and questions. But even just using Pidgin over say regular Facebook is a huge improvement.
With the OTR plugin installed, Go to Tools -> Plugins in Pidgin, Select ‘Off the Record Messaging and hit ‘Configure Plugin’ – Now press ‘Generate’

If all goes well.

Now you will notice a new menu when chatting with Buddies and some new notices

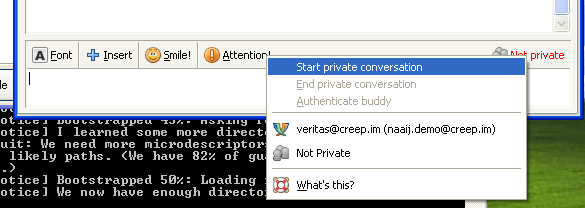
There is a variety of methods of ‘authenticating’ a buddy. The simplest is ‘Manual Fingerprint Verification’ – For your first time encountering people, This is good. It will ensure that your communicating with the same person on the same machine you originally added.

Alternatively there is a secret question and answer. This is good for people you know well. If you know them well enough you wont even need to tell them the answer 🙂

Want to use XMPP on your phone? Get ChatSecure for Android.
Tor is great for a few select cases. Tor by default encrypts everything passing thru it. It also bounces it around a few places and cloaks the original source and destination from all the nodes your data hops over. Tor is not perfect thou. Various website scripts, namely JavaScript, can disclose your true IP Address. Also DNS requests can leak your IP Address. Most websites wont make it a point to attempt to defeat Tor anonymity, but they could.
Want to use Tor on your phone? Get Orbot for Android.
Once the Reset the Net ‘Privacy Pack’ is complete we will link to it here.
Nigel Todman is an Independent Journalist, Technical Consultant, Social Activist, Web Developer and Computer Programmer from Ontario, Canada. Nigel is also the Assistant Webmaster for the NAAIJ. Add him to Facebook and/or Follow him on Twitter E-mail: nigel [at] naaij [dot] org [PGP]